Configuring Time-Based One-Time Password (TOTP) on OpenStack
Author: Ramon Grullon
Introduction
Horizon added time-based one-time password (TOTP) authentication support, leveraging the already existing two factor authentication from Keystone. Now, if a user activates TOTP on Keystone, it gets activated on Horizon too.
Prerequisites
- A working OpenStack 2023.2 environment deployed using Kolla Ansible.
- Keystone and Horizon reconfigured with TOTP enabled
- Admin access to the OpenStack dashboard and CLI.
- Access to the kolla-ansible configuration files.
Create and Configure a TOTP Credential
On one of your control nodes with OpenStack CLI configured:
TOTP uses a base32 encoded string for the secret. The secret must be at least 128 bits (16 bytes). The following bash code can be used to generate a TOTP secret:
echo "iam16characters." | base32 | tr -d "="
Example output:
GEZDGNBVGY3TQOJQGEZDGNBVGY
Configure credentials and MFA rules for user
Create and configure a user to utilize TOTP
openstack user create --project admin --domain default --project-domain default --password-prompt --enable-multi-factor-auth --multi-factor-auth-rule password,totp mfa-member
openstack role add --user mfa-member --project admin member
openstack credential create --type totp mfa-member GEZDGNBVGY3TQOJQGEZDGNBVGY
Set Up TOTP
This typically involves scanning a QR code with a TOTP app like Google Authenticator. On a device install Google Authenticator and inside the app click on ‘Set up account’ and then click on ‘Enter provided key’. In the input fields enter account name and secret.
To quickly verify your configuration you can use https://totp.app and enter your secret to get your code.
Verify TOTP Authentication
Log out of the OpenStack dashboard.
Attempt to log back in. After entering your password, you should be prompted to enter your TOTP code.
Enter TOTP Code:
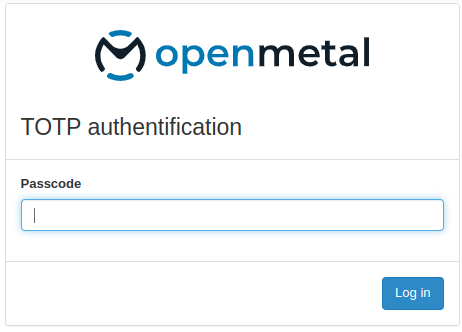
Open your TOTP app and enter the current code to complete the login process.
By following these steps, you should have successfully enabled TOTP authentication in OpenStack 2023.2 using Kolla Ansible, allowing users to enhance the security of their accounts with TOTP through the Horizon dashboard.