In this article
- Why Segment Your Cloud Network?
- Challenges and Risks to Consider
- Common and More Advanced Segmentation Techniques
- Vendor-Specific Approaches: The OpenMetal Example
- Best Practices for Successful Network Segmentation
- Wrapping Up – Network Segmentation Benefits and Risks in Private Clouds
- Interested in OpenMetal Cloud?
Dividing a private cloud network into smaller, isolated segments can improve security and performance while helping manage costs. This practice, known as network segmentation, works by controlling traffic flow between different parts of your network, effectively creating secure zones for specific workloads or functions.
However, it’s not without its complexities and potential downsides. Let’s explore how segmentation works, its advantages, the challenges involved, and practical ways to implement it, including advanced techniques available in some environments.
Why Segment Your Cloud Network?
Implementing network segmentation in a private cloud environment comes with a number of advantages:
Improved Security
By isolating network segments, you limit the potential impact of a security breach. If one segment is compromised, the segmentation boundaries act as barriers, preventing attackers from easily moving laterally to other parts of the network. This containment reduces the “blast radius” of an incident and helps protect sensitive data and critical workloads stored in different segments. You can apply specific security policies and controls tailored to the risk profile of each segment.
Better Performance
Segmentation can reduce network congestion. By confining traffic within specific segments or directing it along optimized paths, you prevent unrelated workloads from competing for bandwidth. Techniques like link aggregation (bonding) can further boost throughput and provide resilience for critical paths.
In environments offering dedicated resources per segment (like some bare metal cloud setups), this isolation can lead to noticeable performance improvements for demanding applications by removing the problem of resource contention.
More Predictable Costs
While segmentation itself can introduce some overhead (more on that later), certain private cloud models that employ segmentation, particularly those with fixed hardware allocation or clear usage-based billing per segment, can make costs more predictable. This avoids the variable egress fees and fluctuating resource costs sometimes seen in public clouds. Many users of these specific private cloud models report significant savings (here at OpenMetal, we’ve seen this commonly ranging from 30% to 60% for our customers coming from public cloud).
Simplified Management and Compliance
Grouping related resources (like development servers, production databases, or specific application tiers) into segments can make the network easier to understand and manage. It also simplifies applying specific policies, access controls, or configurations consistently across groups of assets.
Segmentation is also often a key requirement for meeting compliance standards (like PCI DSS or HIPAA) that mandate the separation of sensitive data environments.
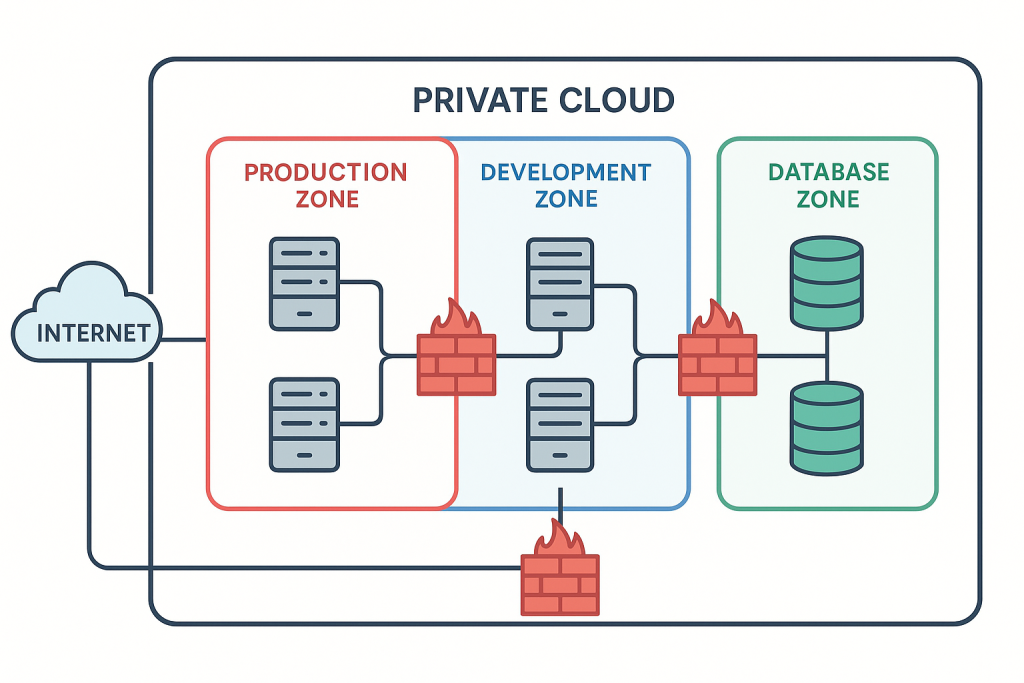
Challenges and Risks to Consider
Despite the benefits, setting up and managing network segmentation involves several challenges:
Implementation Complexity
Designing and setting up a segmented network requires careful planning. You need to define segment boundaries, map communication flows between segments, configure firewall rules, set up VLANs or subnets, and manage IP addressing schemes.
Configuring advanced features like VLAN trunking or link aggregation (bonding) requires specific expertise (e.g., familiarity with OS-level network configuration tools like nmcli, netplan, or ifconfig) and careful validation to avoid misconfigurations.
Management Overhead
Maintaining a segmented network is an ongoing task. It requires continuous monitoring, regular updates to rules and policies as application needs change, and potentially more complex troubleshooting when issues pop up across segment boundaries.
Resource Overhead
Depending on the segmentation strategy, you might need additional hardware or virtual resources for firewalls, routers, monitoring tools, or even duplicated services within isolated segments.
Potential Performance Trade-offs
While segmentation can improve performance by reducing contention, it can also introduce latency. Traffic needing to cross segment boundaries often passes through firewalls or other inspection points, which can add slight delays. Security inspections (like deep packet inspection) required between segments can also consume processing power and potentially reduce throughput compared to a flat, unsegmented network.
Scalability Complexity
While individual segments might scale easily, managing the interactions and policies between a growing number of segments can become increasingly complex.
Common and More Advanced Segmentation Techniques
Segmentation can be achieved through different methods, often used in combination:
Network Isolation (VLANs/Subnets)
Using Virtual LANs (VLANs – following the IEEE 802.1q standard) and IP subnets to create logically separate broadcast domains and network address spaces. This is a fundamental technique for separating traffic.
Multiple Physical Interfaces
Utilizing servers with multiple Network Interface Controllers (NICs) to dedicate physical ports to different types of traffic (e.g., public internet, private backend communication, storage network access). This provides physical separation and dedicated bandwidth.
Link Aggregation (Bonding/LACP)
Combining multiple physical ports into a single logical interface (a ‘bond’). This is commonly done using Link Aggregation Control Protocol (LACP). Benefits include:
- Increased Bandwidth: Aggregates the capacity of the included ports.
- Redundancy: Provides fault tolerance; if one physical link in the bond fails, traffic continues over the remaining active links.
VLAN Trunking (IEEE 802.1q)
Configuring ports (especially useful on bonded ports for combined bandwidth/redundancy) to carry traffic for multiple VLANs simultaneously. Each data frame is tagged with its corresponding VLAN ID. This allows a single physical connection (or bond) to serve several isolated logical networks, enabling flexible and granular segmentation controlled at the server and switch levels without needing a separate physical port for every single network.
Access Controls
Implementing firewall rules (perimeter and internal) to strictly control which traffic is allowed to flow between segments. Role-Based Access Control (RBAC) is crucial for managing user and service permissions within and across segments.
Resource Allocation
Assigning specific compute, memory, and storage quotas or dedicated hardware to different segments to guarantee resources and performance.
Traffic Management
Using routing policies and potentially traffic shaping tools to direct and control data flow patterns.
Micro-segmentation
A more granular approach where security policies are applied to individual workloads or applications, often independent of the underlying network topology, using software-defined networking (SDN) or specialized agents.
Vendor-Specific Approaches: The OpenMetal Example
S ome private cloud providers offer specific segmentation architectures built on bare metal. At OpenMetal, for instance, we provide bare metal servers equipped with multiple physical network interfaces (NICs – e.g., dual 10Gbps or faster ports) as part of our private cloud solutions.
ome private cloud providers offer specific segmentation architectures built on bare metal. At OpenMetal, for instance, we provide bare metal servers equipped with multiple physical network interfaces (NICs – e.g., dual 10Gbps or faster ports) as part of our private cloud solutions.
A key aspect of our approach is giving users root-level access. This allows users to directly configure advanced networking features like link aggregation (LACP bonding) for throughput/redundancy and VLAN trunking (802.1q) directly on these physical interfaces or bonds. This capability supports highly customized and granular network segmentation, allowing separation of public traffic, private management networks, storage access, and application tiers using distinct VLANs over potentially bonded, high-throughput connections, all managed by the user at the OS level.
Through our approach and technology, we’re able to offer rapid deployment times, predictable cost models, superior performance, and high levels of customization – a contrast to typical public cloud.
Best Practices for Successful Network Segmentation
To navigate the challenges and maximize the benefits of segmentation:
Plan Thoroughly
Define clear goals for segmentation (e.g., security zones, compliance boundaries, performance isolation for specific tiers). Map out application dependencies and required communication paths before you start implementing. Decide if you need simple VLAN separation or more advanced setups like bonding and trunking.
Document Everything
Maintain clear, up-to-date documentation of your network topology, segment boundaries, IP addressing, VLAN IDs, bond configurations, firewall rules, and access policies.
Start Simple (If Possible)
Begin with broader segments and refine them over time if necessary, rather than starting with extreme granularity unless required. Master basic VLAN separation before getting into complex trunking across multiple bonds, for instance.
Use Automation
Employ automation tools (like Ansible, Terraform) for provisioning segments, applying network configurations (including bond and VLAN setups), managing firewall rules, and ensuring policy consistency. This reduces manual errors and speeds up changes.
Implement Strong Access Controls
Use the principle of least privilege. Default to denying traffic between segments and explicitly allow only necessary communication using firewall rules. Use RBAC effectively.
Leverage Physical and Logical Separation
Use multiple NICs, bonding, and VLANs strategically to create both physical and logical separation where needed for security or performance.
Monitor Continuously
Use network monitoring tools to track performance (latency, throughput, utilization of individual ports and bonds) within and between segments, watch for security anomalies (using IDS/IPS if appropriate), and log traffic flows (especially at segment boundaries/firewalls).
Regularly Review and Audit
Periodically review your segmentation policies, firewall rules, VLAN configurations, and access controls to ensure they are still relevant and effective. Conduct security audits to identify potential weaknesses or misconfigurations. Optimize performance based on monitoring data.
Wrapping Up – Network Segmentation Benefits and Risks in Private Clouds
Network segmentation is a powerful technique for improving the security, performance, and manageability of private cloud environments. Taking advantage of features from basic VLANs to advanced techniques like multi-port bonding and VLAN trunking allows for sophisticated network designs. However, it requires careful planning, diligent management, and an understanding of the potential trade-offs in complexity and overhead.
By weighing the benefits against the risks, choosing appropriate techniques, and following best practices, organizations can build more resilient and efficient private cloud infrastructures customized to their needs. The right approach will depend on your priorities around security posture, performance requirements, budget constraints, and operational capabilities.
Schedule a Consultation
Get a deeper assessment and discuss your unique requirements.
Read More on the OpenMetal Blog



































