In this article
We examine why enterprise buyers require confidential computing, specific questions TDX helps you answer, how to position TDX as a competitive advantage, real implementation scenarios, ROI calculations showing TDX pays for itself with a single enterprise deal, and practical steps to deploy TDX on OpenMetal infrastructure.
Your SaaS company has product-market fit. You’re growing 50% year-over-year. Revenue hit $10 million and you’re targeting $25 million next year. The next phase of growth requires moving upmarket to enterprise customers with six-figure annual contracts.
Then you encounter the enterprise security questionnaire. Pages of questions about data encryption, access controls, tenant isolation, and compliance certifications. Questions about how you protect data at runtime, not just at rest or in transit. Questions your current infrastructure can’t answer the way enterprise buyers want to hear them.
Your competitor answers these questions differently. They mention confidential computing, hardware-level encryption, and cryptographically verified isolation. They’re using Intel Trust Domain Extensions (TDX) to provide guarantees you can’t match. They win the deal.h
This scenario plays out repeatedly as mid-market companies try to break into enterprise accounts. Security requirements that seemed theoretical suddenly become deal-breakers. This guide shows you how Intel TDX on bare metal infrastructure helps mid-market SaaS companies answer enterprise security questions, differentiate from competitors, and close deals worth 10x your typical contract size.
The Enterprise Sales Challenge for Mid-Market Companies
Mid-market SaaS companies face a consistent problem when pursuing enterprise deals. You built infrastructure that works great for your current customers. It scales well, costs are reasonable, and reliability is solid. Then you enter enterprise sales cycles and discover your infrastructure doesn’t check the boxes enterprise procurement requires.
Security Requirements Get Serious
Small and medium businesses care about security, but they’re generally satisfied with standard practices like encryption at rest, TLS for data in transit, and proper access controls. Enterprise buyers dig deeper.
They want to know what happens when data is being processed. Who can access memory while your application runs? Can cloud administrators see customer data? What prevents other tenants from accessing data if there’s a hypervisor vulnerability? How do you cryptographically prove isolation between customers?
These questions aren’t theoretical. They come directly from enterprise security teams who have seen breaches, dealt with compliance audits, and need to explain their vendor choices to boards of directors. They’re looking for specific technical controls, not general assurances.
RFPs Include Confidential Computing Requirements
Request for Proposals from enterprise buyers increasingly include confidential computing as a requirement or significant scoring factor. The RFP might ask:
“Does your platform support hardware-based trusted execution environments for customer data processing?”
“Can you provide cryptographic attestation that customer workloads run in isolated, encrypted enclaves?”
“What hardware-level protections prevent unauthorized access to customer data during processing?”
If you can’t answer yes with technical specifics, you’re at a disadvantage against competitors who can. RFP scoring often allocates 20-30% of points to security capabilities. Missing confidential computing requirements can knock you out of contention before you even present.
Compliance Audits Favor Advanced Security
Enterprise customers in regulated industries (finance, healthcare, government) undergo regular compliance audits. Their vendors get scrutinized as part of these audits. Auditors ask detailed questions about data protection controls.
Having SOC 2 Type II certification is table stakes. Enterprise buyers want to know what additional controls you have. Confidential computing provides auditable, verifiable protection that goes beyond standard compliance frameworks. This makes their audits easier and reduces their risk exposure from vendor relationships.
Competitors Are Already There
The most frustrating part? While you’re trying to figure out how to answer these questions, established competitors already have confidential computing deployed. They’re using it in sales presentations, highlighting it in security documentation, and winning deals based on this capability.
These competitors aren’t necessarily better products or larger companies. They just recognized earlier that enterprise security requirements were changing and built infrastructure to meet those requirements. Now they have a competitive moat you need to overcome.
What Enterprise Buyers Actually Require
Let’s get specific about what enterprise security teams want to see. These requirements come directly from real RFPs, security questionnaires, and procurement discussions.
Memory Encryption During Processing
Enterprise buyers understand that encrypting data at rest (on disk) and in transit (over networks) is standard. They want to know about the gap in between – when data is loaded into memory for processing.
Traditional infrastructure decrypts data when loading it into RAM so the CPU can process it. This creates a window where administrators, hypervisor compromises, or other tenants could potentially access that data. Enterprise security teams want this gap closed.
Intel TDX addresses this by keeping data encrypted in memory. Even when the CPU is actively processing data, it remains encrypted using per-VM encryption keys. This means:
- Cloud administrators can’t access customer data in memory
- Hypervisor vulnerabilities don’t expose data across VMs
- Physical memory access (cold boot attacks) reveals only encrypted data
- Side-channel attacks are significantly harder
When an enterprise buyer asks “How is our data protected during processing?”, you can point to hardware-level memory encryption as the answer.
Cryptographic Attestation of Environment
Enterprise buyers don’t want to take your word that security controls are in place. They want cryptographic proof. This is where attestation becomes critical.
Intel TDX provides remote attestation capabilities. Before loading sensitive data into a Trust Domain (TD), the enterprise customer can verify:
- The TD is running on genuine Intel hardware with TDX enabled
- The firmware and software stack matches expected measurements
- No unauthorized software is present in the TD
- The TD is properly isolated from other workloads
This attestation happens cryptographically through Intel’s attestation services. The enterprise customer can verify this independently without trusting your assurances. It’s mathematical proof rather than policy documentation.
When security questionnaires ask “How do customers verify their data is properly protected?”, attestation provides a technical answer that satisfies enterprise security teams.
Tenant Isolation Guarantees
Multi-tenant SaaS architecture creates concerns for enterprise buyers. They worry about:
- What if another tenant exploits a vulnerability to access our data?
- What if a rogue employee tries to access specific customer data?
- How do we know our workloads are truly isolated?
Intel TDX provides hardware-enforced isolation. Each Trust Domain runs in its own encrypted memory space with cryptographic separation. Even the hypervisor can’t access TD memory. This creates stronger isolation than traditional virtualization.
For enterprise buyers, this means they can use multi-tenant SaaS with confidence that hardware-level controls prevent cross-tenant access, not just software policies. This often satisfies security teams that would otherwise require dedicated infrastructure or on-premises deployment.
Supply Chain Security
Enterprise security teams worry about supply chain attacks where malicious code gets inserted into the software stack. TDX’s attestation helps here too.
The attestation process measures the entire software stack (firmware, kernel, application) before allowing sensitive data to load. If something in the stack doesn’t match expected measurements, attestation fails and the workload won’t start with production data.
This provides defense against:
- Compromised firmware updates
- Malicious kernel modules
- Unauthorized software in the stack
- Configuration tampering
When enterprise buyers ask about supply chain security, TDX attestation demonstrates concrete technical controls beyond vendor security policies.
How TDX Answers Enterprise Security Questions
Let’s walk through specific questions from enterprise security questionnaires and how TDX enables you to answer them effectively.
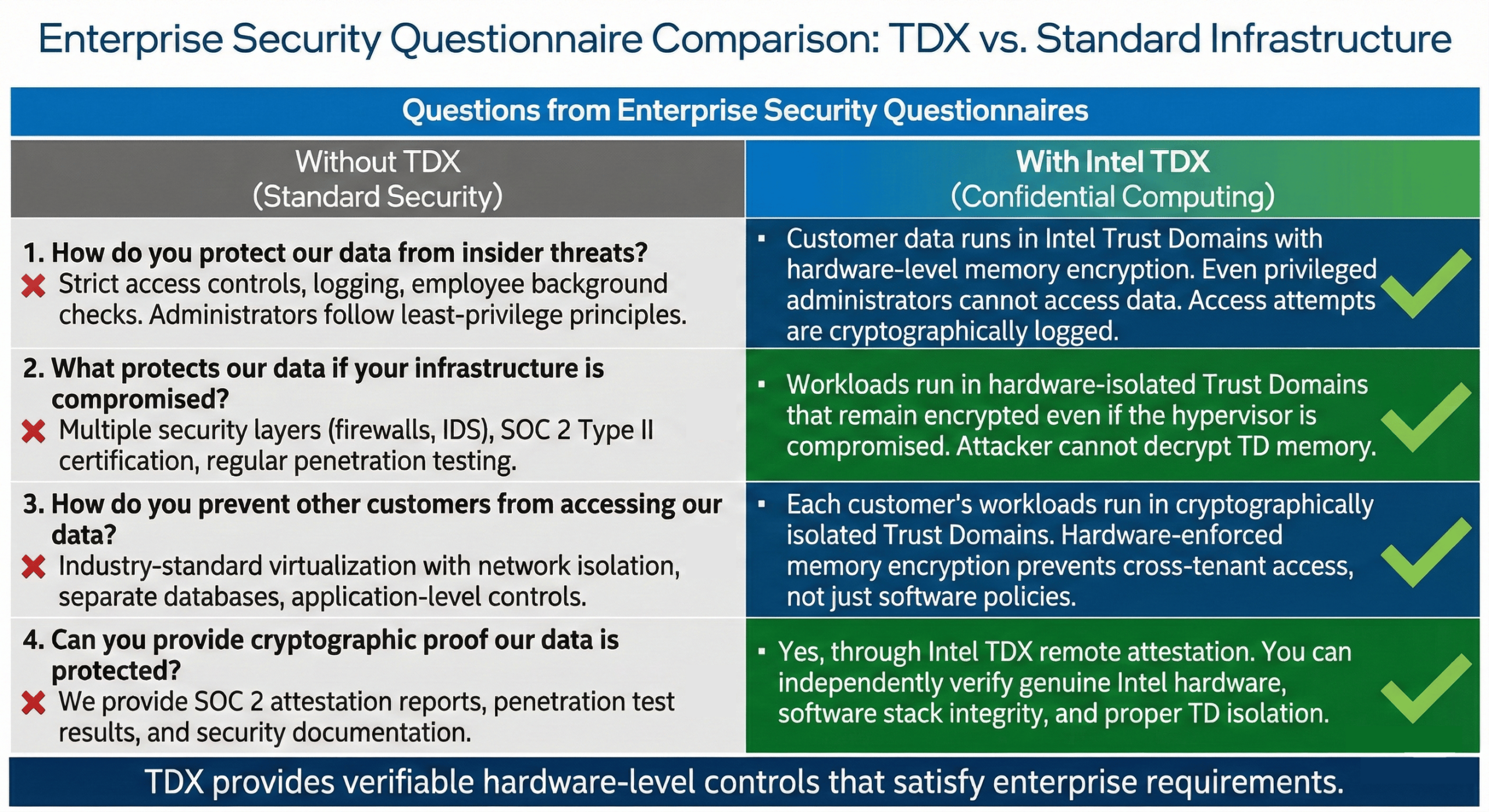
“How do you protect our data from insider threats?”
Without TDX: “We have strict access controls, logging, and employee background checks. Administrators follow least-privilege principles and all access is audited.”
With TDX: “Customer data runs in Intel Trust Domains with hardware-level memory encryption. Even privileged administrators cannot access data in Trust Domains. All access attempts are cryptographically logged. The hardware prevents insider access to customer data during processing.”
The TDX answer is more concrete and technically verifiable. It doesn’t rely on trusting your processes; it points to hardware controls.
“What protects our data if your infrastructure is compromised?”
Without TDX: “We have multiple security layers including firewalls, intrusion detection, and security monitoring. We maintain SOC 2 Type II certification and conduct regular penetration testing.”
With TDX: “Customer workloads run in hardware-isolated Trust Domains that remain encrypted even if the hypervisor or host OS is compromised. An attacker gaining administrative access cannot decrypt Trust Domain memory because encryption keys are hardware-protected and never exposed to software.”
This addresses the “what if you get hacked?” question that keeps enterprise security teams awake at night.
“How do you prevent other customers from accessing our data?”
Without TDX: “We use industry-standard virtualization with strict network isolation, separate databases per customer, and application-level access controls. Each customer’s data is logically separated.”
With TDX: “Each customer’s workloads run in cryptographically isolated Trust Domains. Hardware-enforced memory encryption with per-domain keys ensures other tenants cannot access your data even if they exploit application or hypervisor vulnerabilities. Isolation is enforced by the CPU, not just software.”
Hardware-enforced isolation is stronger than software-enforced isolation. Enterprise buyers understand this distinction.
“Can you provide cryptographic proof our data is protected?”
Without TDX: “Yes, we provide SOC 2 attestation reports, penetration test results, and security documentation showing our controls are properly implemented.”
With TDX: “Yes, through Intel TDX remote attestation. Before loading your data, you can cryptographically verify: (1) your workload runs on genuine Intel hardware with TDX enabled, (2) the software stack matches expected measurements, (3) the Trust Domain is properly isolated. This verification happens independently without relying on our attestations.”
This is a game-changer. You’re offering mathematical proof rather than audit reports.
“What happens if a vulnerability is discovered in the virtualization layer?”
Without TDX: “We monitor security advisories and apply patches quickly. We have a 24-hour SLA for critical security updates. We maintain redundant infrastructure to minimize downtime during security maintenance.”
With TDX: “Trust Domains are isolated from the virtualization layer. Even if a hypervisor vulnerability is exploited, the attacker cannot access encrypted Trust Domain memory because the CPU enforces isolation. This provides defense-in-depth beyond patching.”
You’re showing that vulnerabilities don’t automatically mean data exposure.
Competitive Differentiation with TDX
Beyond answering security questions, TDX becomes a competitive weapon when positioned correctly.
Positioning Against Larger Competitors
Larger, established SaaS companies have advantages in brand recognition, customer references, and sales resources. You need technical differentiators that matter to buyers.
Confidential computing is one of those differentiators. Many large SaaS companies built infrastructure years ago and haven’t upgraded to confidential computing. They’re running on older platforms or public cloud infrastructure that doesn’t support TDX.
You can position your company as:
- More technically advanced in security architecture
- Purpose-built for modern security requirements
- Using latest hardware security features
This narrative works because it’s true and verifiable. Enterprise buyers can check whether competitors support confidential computing. If they don’t, you have a concrete advantage.
Winning Against Public Cloud Players
Some enterprise buyers consider building on public cloud platforms directly rather than using your SaaS product. They think running on AWS or Azure gives them better security because those platforms are “enterprise-grade”.
TDX on bare metal infrastructure provides stronger guarantees than public cloud virtualized environments:
Hardware-enforced isolation: Bare metal TDX means the hardware is dedicated to your workload. Public cloud adds hypervisor layers that increase attack surface.
No noisy neighbors: Dedicated hardware eliminates performance variability and side-channel risks from other tenants on shared physical hosts.
Full control: You control the firmware, hypervisor, and entire stack. Public cloud requires trusting the provider’s infrastructure configuration.
Cost predictability: Bare metal infrastructure has fixed monthly costs. Public cloud charges per-resource with variable costs that can spike unexpectedly.
This helps you win against both “buy SaaS from a different vendor” and “build on public cloud ourselves” alternatives.
Creating Pricing Power
Security capabilities create pricing power. Enterprise buyers pay premium prices for products with superior security because security failures are expensive.
Companies like Snowflake and Databricks command higher prices partly because they provide strong security guarantees for sensitive data. TDX enables you to offer similar guarantees and justify higher prices for enterprise plans.
You can create pricing tiers like:
- Standard: Regular multi-tenant infrastructure
- Enterprise: TDX-protected workloads with enhanced isolation
- Enterprise Plus: TDX plus dedicated hardware for ultimate security
The enterprise tiers command 2-3x higher prices, and customers pay because they need the security capabilities. This improves margins while serving fewer customers.
Hypothetical Scenarios: How TDX Could Work for Different Companies
Let’s explore how mid-market companies in different industries might use TDX to address enterprise sales challenges. These are illustrative scenarios based on common patterns we see in the market.
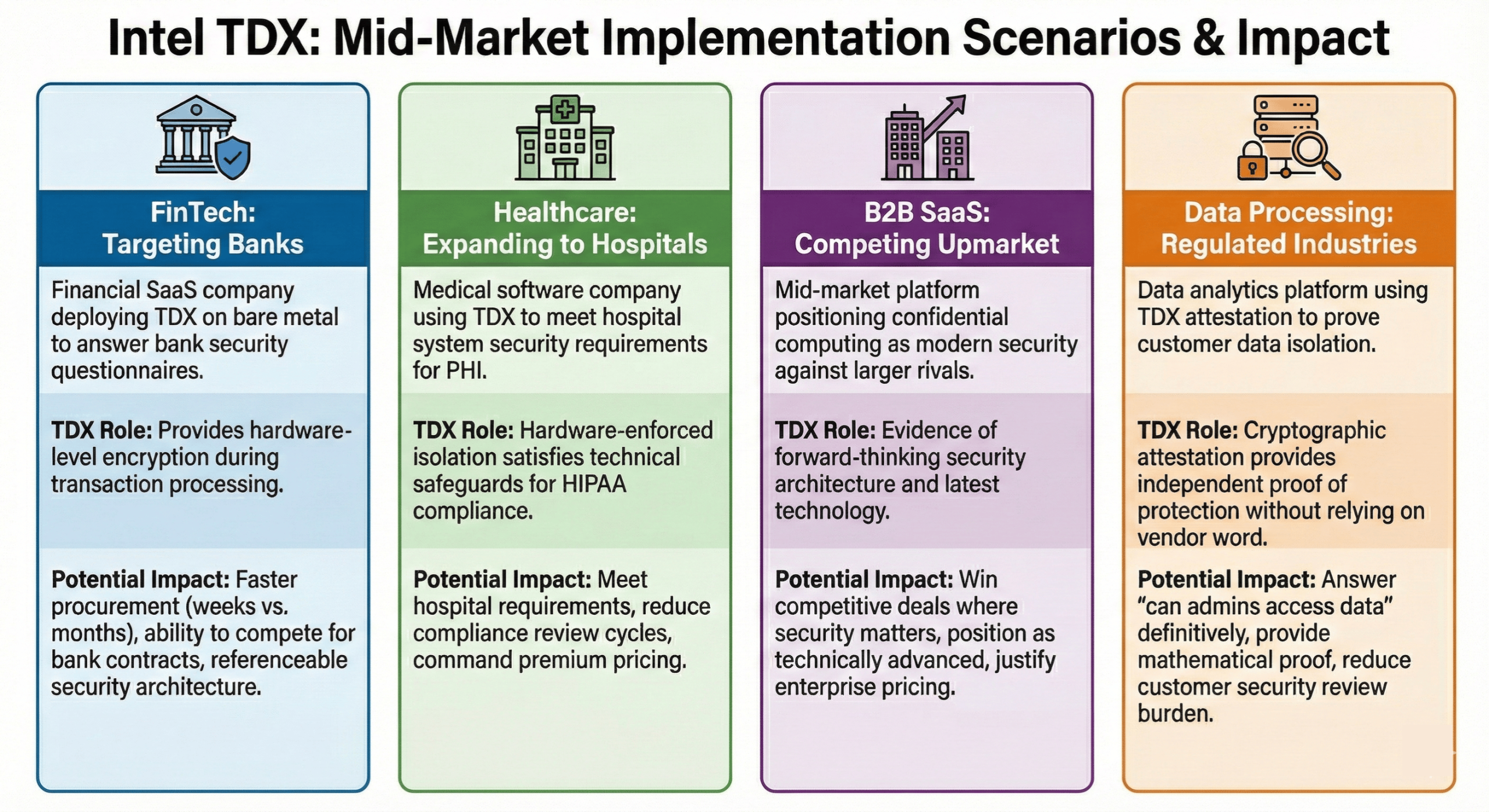
Scenario: FinTech Company Targeting Banking Customers
Typical situation: Financial analytics or payment processing SaaS companies often hit a wall when trying to sell to banks. Regional banks and credit unions may accept standard security practices, but major banks have procurement teams that require specific technical controls.
Common challenge: Bank security questionnaires ask about hardware-based confidential computing and cryptographic attestation. Without these capabilities, companies either don’t make it past procurement or face 6-12 month security review cycles that kill deals.
How TDX could help: A financial SaaS company deploying TDX on bare metal infrastructure could answer bank security requirements directly. When the questionnaire asks “Do you support hardware-based trusted execution environments?”, the answer becomes “Yes, we use Intel TDX for hardware-level memory encryption during transaction processing.”
Potential impact:
- Faster procurement approval (weeks instead of months)
- Ability to compete for contracts previously out of reach
- Reference-able security architecture that satisfies bank compliance teams
- Differentiation from competitors using standard cloud infrastructure
Key success factor: The bank’s CISO needs to explain security architecture to the board and auditors. “Hardware-level encryption that prevents unauthorized access during processing” is a clear, understandable security story that passes audit review.
Scenario: Healthcare SaaS Expanding to Hospital Systems
Typical situation: Medical software companies serving small practices and clinics find that hospital systems have dramatically different security requirements. HIPAA compliance is table stakes, but large hospital systems want specific technical controls beyond standard compliance frameworks.
Common challenge: Hospital procurement teams increasingly require hardware-level protection for Protected Health Information (PHI) during processing. They’ve seen enough breaches to know that encryption at rest and in transit isn’t enough. They want technical safeguards that go beyond policy.
How TDX could help: A healthcare SaaS company could implement confidential computing specifically for PHI processing workloads. This provides hardware-enforced isolation that satisfies technical safeguards requirements under HIPAA.
Potential impact:
- Meet hospital system security requirements that competitors can’t match
- Reduce compliance review cycles significantly
- Provide documentation for hospital compliance teams to use in their own audits
- Command premium pricing for hospital system plans
Key success factor: Hospital compliance teams need to document specific technical controls that exceed typical implementations. Hardware-enforced isolation and encrypted processing give them concrete controls to point to during audits.
Scenario: B2B SaaS Platform Competing Against Larger Players
Typical situation: Mid-market B2B platforms often build superior products but struggle to win enterprise deals against established competitors. The product might be better and cheaper, but enterprise buyers gravitate toward “safe” choices from well-known vendors.
Common challenge: When competing against companies like Salesforce, Workday, or ServiceNow, product features alone don’t close deals. Enterprise buyers want assurance that the vendor has enterprise-grade security architecture. Many established vendors haven’t upgraded to confidential computing, creating an opportunity.
How TDX could help: A mid-market platform could position confidential computing as evidence of modern, forward-thinking security architecture. “We’re using the latest Intel security technology” becomes a differentiator when competing against vendors on older infrastructure.
Potential impact:
- Win competitive deals where security matters
- Position as more technically advanced despite smaller company size
- Justify premium pricing for enterprise tier
- Create defensible competitive moat
Key success factor: Enterprise buyers need to justify choosing a smaller vendor over established players. Superior security architecture provides a concrete reason beyond just “better product” or “cheaper price”.
Scenario: Data Processing Platform Serving Regulated Industries
Typical situation: Companies providing data analytics, ETL, or processing services for customers in regulated industries (finance, healthcare, government) face intense scrutiny on how they handle customer data.
Common challenge: Customers increasingly ask “Can your administrators access our data?” and “How do you prove other customers can’t access our data?” Standard answers about access controls and logging don’t fully satisfy enterprise security teams who’ve seen insider threat breaches.
How TDX could help: A data processing platform could implement TDX for customer workloads and provide cryptographic attestation. This lets customers verify independently that their data is properly isolated and encrypted, without trusting the vendor’s assurances.
Potential impact:
- Answer the “can admins access data” question definitively (no, hardware prevents it)
- Provide proof through attestation rather than policy
- Win customers who would otherwise require on-premises deployment
- Reduce customer security review burden
Key success factor: Customers can verify protection through attestation rather than auditing the vendor’s processes. This shifts from “trust us” to “verify mathematically”.
Common Patterns Across Industries
These scenarios share several patterns that apply broadly:
Pattern 1: Enterprise Procurement Requirements
As companies move upmarket, they encounter procurement processes with specific technical requirements. Confidential computing appears in RFPs across industries as enterprise buyers become more sophisticated about security.
Companies without these capabilities get filtered out early in procurement. Companies with confidential computing can participate in opportunities previously unavailable to them.
Pattern 2: Compliance Differentiation
In regulated industries, security beyond standard compliance frameworks creates competitive advantage. Most vendors meet baseline requirements (SOC 2, HIPAA, etc.). Hardware-level security provides differentiation that matters to compliance teams.
This is especially valuable when competing against established vendors who haven’t upgraded infrastructure to support confidential computing.
Pattern 3: Trust Through Verification
Enterprise buyers prefer verification over trust. Cryptographic attestation provides mathematical proof rather than requiring customers to trust vendor policies and processes.
This dramatically reduces the security review burden for enterprise buyers and shortens sales cycles.
Pattern 4: Justification for Premium Pricing
Advanced security capabilities justify higher prices. Enterprise buyers pay premiums for products with superior security because security failures are expensive. TDX enables companies to create higher-priced enterprise tiers with defensible value propositions.
Pattern 5: Reference Architecture Advantage
Once you have confidential computing deployed, it becomes a reference architecture that sales teams can point to. “We use Intel TDX for hardware-level encryption” is a concrete, verifiable claim that stands up to technical scrutiny.
This is more powerful than vague security claims that all vendors make.
Real-World Context
While the scenarios above are illustrative, the underlying dynamics are real. Enterprise buyers across industries are asking more sophisticated security questions. RFPs increasingly include confidential computing requirements. Security teams want hardware-level controls, not just software policies.
Mid-market companies that implement these capabilities early have advantages over competitors who haven’t yet made the investment. The infrastructure costs are modest relative to enterprise contract values, making the ROI calculation straightforward for companies serious about moving upmarket.
ROI and Business Case
Let’s break down the actual economics of deploying TDX to understand the business case.
Infrastructure Costs
Intel TDX requires specific memory configurations. OpenMetal’s XL V4 and XXL V4 bare metal servers are TDX-ready out of the box. Medium V4 and Large V4 servers can be upgraded with TDX-compatible RAM to support confidential computing workloads.
Currently, TDX is available on OpenMetal’s bare metal servers. Full integration with OpenStack private cloud orchestration is under development.
TDX-ready bare metal configurations (no upgrade needed):
XL V4 Bare Metal:
- Monthly cost: $1,987.20 (US locations)
- Hardware: 64C/128T CPU, 1024GB RAM, 4× 6.4TB NVMe, 6Gbps bandwidth
- Intel Xeon Gold processors with TDX-compatible RAM
- TDX-ready out of the box
XXL V4 Bare Metal:
- Monthly cost: $2,779.20 (US locations)
- Hardware: 64C/128T CPU, 2048GB RAM, 6× 6.4TB NVMe, 10Gbps bandwidth
- Intel Xeon Gold processors with TDX-compatible RAM
- TDX-ready out of the box
Upgradeable bare metal configurations (RAM upgrade required for TDX):
Large V4 Bare Metal (with RAM upgrade):
- Monthly cost: $1,173.60 (US) + RAM upgrade cost
- Hardware: 32C/64T CPU, 512GB RAM, 2× 6.4TB NVMe, 4Gbps bandwidth
- Requires TDX-compatible RAM upgrade
Medium V4 Bare Metal (with RAM upgrade):
- Monthly cost: $619.20 (US) + RAM upgrade cost
- Hardware: 24C/48T CPU, 256GB RAM, 6.4TB NVMe, 2Gbps bandwidth
- Requires TDX-compatible RAM upgrade
For most mid-market companies targeting enterprise deals, starting with one or more XL V4 bare metal servers provides the right balance of capacity and TDX readiness without requiring hardware modifications.
For comparison, equivalent dedicated compute on AWS with confidential computing capabilities would cost significantly more, with additional egress charges that OpenMetal includes.
Additional costs:
- Engineering time to implement TDX (typically 2-4 weeks)
- Documentation and sales materials update (1-2 weeks)
- Sales training on confidential computing messaging (ongoing)
- RAM upgrade costs (if choosing Medium or Large V4)
Total initial investment for TDX-ready infrastructure: Starting at $1,987.20/month (single XL V4 bare metal) + roughly $20-40K in engineering and sales prep work. Most deployments use multiple servers for redundancy and capacity.
Revenue Impact
The ROI comes from landing larger enterprise contracts.
Typical mid-market deal: $20-50K annually
Enterprise deal with TDX as differentiator: $200-600K annually
Let’s work through a conservative example:
Scenario: $10M ARR SaaS company targeting enterprise growth
Without TDX:
- Average contract: $35K annually
- Enterprise conversion rate: 10%
- Enterprise deals closed per year: 2-3
- Enterprise revenue: $70-105K
With TDX:
- Average enterprise contract: $300K annually
- Enterprise conversion rate: 25% (improved win rate)
- Enterprise deals closed per year: 5-6
- Enterprise revenue: $1.5M-1.8M
Net impact: $1.4-1.7M additional annual revenue from enterprise deals
ROI calculation:
- Investment: ~$64K first year ($1,987.20/month × 12 months × 2 servers for redundancy + $20K implementation)
- Additional revenue: $1.5M annually (conservative)
- ROI: 2,244%
- Payback period: Less than 2 months
Even if you close just one additional $500K enterprise deal because of TDX capabilities, the investment pays for itself nearly 8x in the first year.
Non-Financial Benefits
Beyond direct revenue, TDX provides additional benefits:
Faster sales cycles: Security objections get resolved faster when you can point to hardware-level controls instead of explaining software policies. This can cut enterprise sales cycles by 30-50%.
Higher win rates: When competing against vendors without confidential computing, you have a clear technical advantage. This improves win rates in competitive situations.
Customer retention: Enterprise customers with strong security requirements are more likely to stick with vendors who meet their needs. This improves retention and expansion revenue.
Brand perception: Being positioned as security-forward improves brand perception with enterprise buyers. This creates halo effects across all enterprise sales efforts.
Recruiting advantage: Engineers want to work on modern infrastructure with advanced security capabilities. TDX deployment can help attract senior engineering talent.
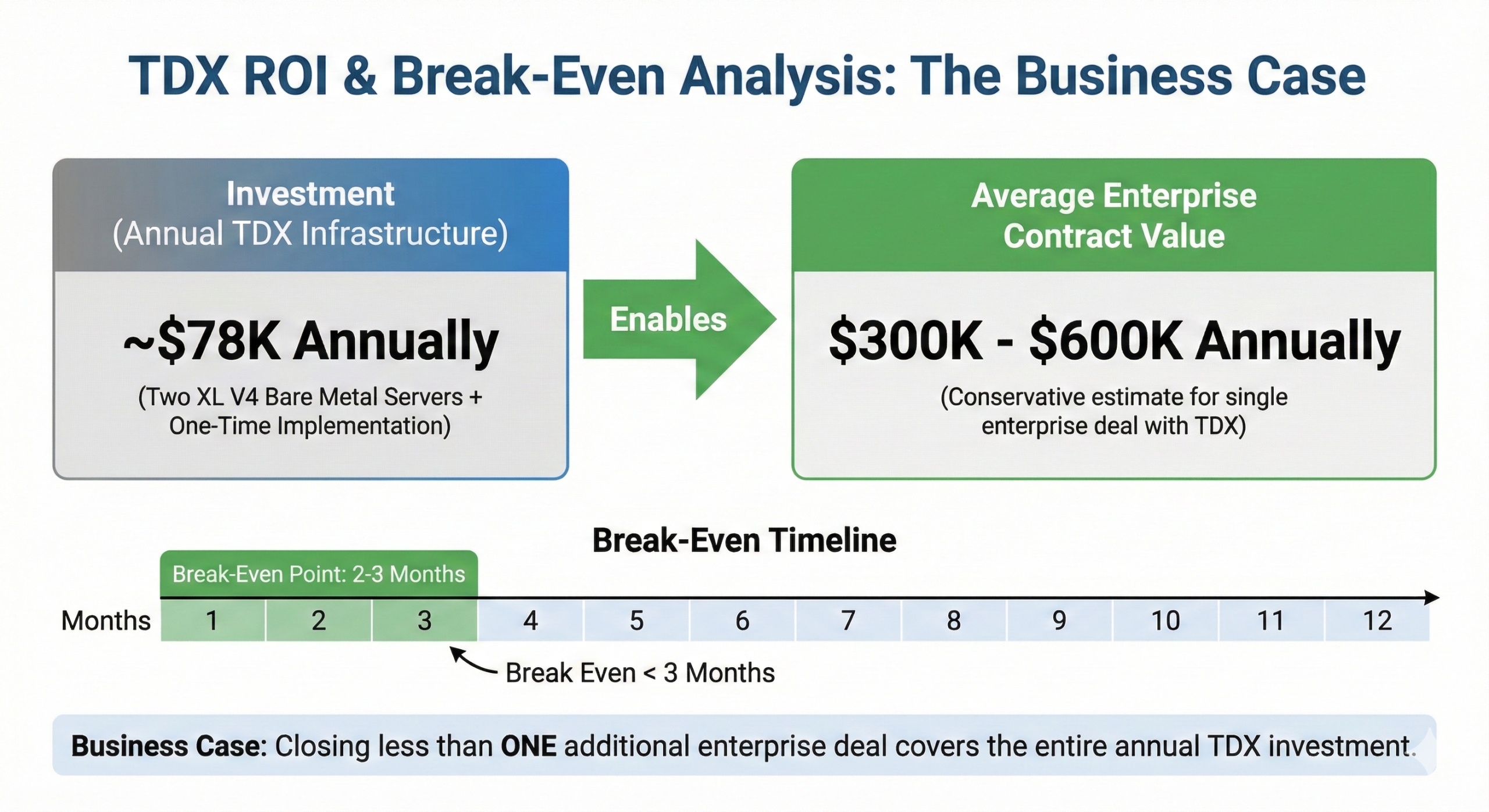
Break-Even Analysis
The business case is straightforward because infrastructure costs are low relative to enterprise contract value.
Monthly TDX infrastructure cost: $3,974.40 (two XL V4 bare metal servers for redundancy)
One-time implementation cost: ~$30K
Annual total cost: ~$78K
Single enterprise contract value: $300-600K annually
You need to close less than one additional enterprise deal to break even. Most mid-market companies pursuing enterprise growth will see positive ROI within 2-3 months of implementation.
Pricing and Packaging Strategies
How you price and package TDX capabilities affects both adoption and margins.
Tiered Security Offerings
Create clear product tiers with TDX as an enterprise feature:
Standard Plan:
- Regular multi-tenant infrastructure
- Standard encryption (at rest and in transit)
- SOC 2 Type II compliant
- Pricing: $X per user/month
Business Plan:
- Enhanced isolation
- Additional security controls
- Priority support
- Pricing: $2X per user/month
Enterprise Plan:
- Intel TDX confidential computing
- Hardware-level memory encryption
- Remote attestation capabilities
- Dedicated security architecture review
- Pricing: $4X per user/month
The Enterprise plan costs 4x but infrastructure costs are only marginally higher. This creates excellent margins on enterprise deals.
Usage-Based Add-On
Alternatively, offer TDX as an add-on to any plan:
Confidential Computing Add-On:
- Intel TDX protection for sensitive workloads
- Cryptographic attestation
- Enhanced compliance support
- Pricing: +50% of base plan cost
This makes TDX available to customers not quite ready for full Enterprise plans but with specific security requirements.
Implementation Services
Some enterprise buyers want help implementing confidential computing properly. This creates services revenue opportunity:
TDX Implementation Service:
- Security architecture review
- TDX deployment and configuration
- Attestation setup and testing
- Documentation for compliance teams
- Pricing: $25-50K one-time
This covers your engineering time while providing value to enterprise customers who need hands-on support.
Competitive Displacement Incentive
When competing against established vendors, offer implementation support to sweeten the deal:
Competitive Replacement Program:
- Free TDX implementation service (normally $25-50K)
- Extended trial period with full TDX capabilities
- Dedicated migration support
- Condition: Migrating from competitor within 90 days
This removes friction from competitive displacements and improves win rates in replacement scenarios.
Getting Started on OpenMetal
Deploying Intel TDX on OpenMetal infrastructure is straightforward. Here’s the practical path forward.
Step 1: Verify TDX Requirements
Confirm your use case benefits from TDX:
Good fit for TDX:
- Processing sensitive customer data (PII, PHI, financial data)
- Multi-tenant SaaS with enterprise customers
- Compliance-heavy industries (finance, healthcare, government)
- Competitive situations where security matters
- Enterprise procurement requiring confidential computing
Maybe not necessary:
- Processing only public data
- Single-tenant deployments with physical isolation
- Use cases where performance overhead is prohibitive
- Customers who don’t value confidential computing
If you’re targeting enterprise customers in regulated industries or dealing with sensitive data, TDX likely makes sense.
Step 2: Plan Your Architecture
Decide which workloads run in Trust Domains:
High priority for TDX:
- Customer data processing
- Authentication and authorization services
- Database workloads with sensitive data
- API services handling customer requests
- Analytics processing customer information
Lower priority:
- Static content serving
- Public API endpoints
- Monitoring and logging infrastructure
- Development and staging environments
- Non-sensitive batch processing
You don’t need to run everything in Trust Domains. Focus on workloads processing the most sensitive data.
Step 3: Deploy Infrastructure
OpenMetal provides bare metal servers with Intel Xeon processors supporting TDX. Currently, TDX is available on bare metal servers. Full OpenStack private cloud integration is under development.
TDX-Ready Bare Metal Servers (Recommended)
Dedicated servers with TDX-compatible hardware out of the box
- XL V4 Bare Metal: $1,987.20/month (US), TDX-ready, no upgrades needed
- XXL V4 Bare Metal: $2,779.20/month (US), TDX-ready, maximum capacity
- Best for: TDX workloads requiring immediate deployment
- Full hardware control and root access for TDX configuration
Upgradeable Bare Metal Servers
Dedicated servers requiring RAM upgrade for TDX compatibility
- Medium V4 or Large V4 Bare Metal: Requires TDX-compatible RAM upgrade
- Best for: Budget-conscious deployments willing to upgrade
- Contact OpenMetal for RAM upgrade pricing and availability
For most mid-market companies deploying TDX for the first time, starting with one or two XL V4 bare metal servers provides the capacity needed for production workloads with TDX protection. Deploy multiple servers for redundancy and load balancing.
All bare metal servers provide full root access and control over TDX configuration. The TDX deployment guide walks through the technical setup process on bare metal infrastructure.
Step 4: Implement TDX Protection
The technical implementation involves:
- Enable TDX in BIOS: Configure processor to support Trust Domains
- Configure hypervisor: Set up KVM or hypervisor with TDX support
- Create Trust Domains: Launch VMs as Trust Domains with encrypted memory
- Implement attestation: Configure remote attestation for customer verification
- Test thoroughly: Validate that TDX protection works correctly
OpenMetal’s support team can assist with technical implementation if needed. The process typically takes 1-2 weeks for experienced teams.
Step 5: Update Sales Materials
Once TDX is deployed, update your go-to-market:
Security documentation:
- Add confidential computing section explaining TDX
- Include attestation procedures for customers
- Document hardware specifications and protections
RFP responses:
- Create templates answering confidential computing questions
- Include technical architecture diagrams showing TDX
- Highlight hardware-level protection capabilities
Sales presentations:
- Add security differentiation slides
- Explain TDX benefits in business terms
- Position against competitors without confidential computing
Website and marketing:
- Update security page with confidential computing details
- Add enterprise security as a key differentiator
- Create case studies (when customers allow)
Step 6: Train Sales Team
Sales teams need to understand confidential computing well enough to position it effectively:
Key concepts to teach:
- What confidential computing protects (data during processing)
- How TDX works (hardware-level memory encryption)
- Why it matters (insider threats, hypervisor compromises, tenant isolation)
- When to emphasize it (enterprise deals, security-focused buyers)
Competitive positioning:
- Which competitors have confidential computing (few)
- How to position TDX against public cloud options
- Handling objections about complexity or performance
Customer conversations:
- How to explain TDX to non-technical buyers
- Connecting security capabilities to business value
- Using attestation as proof point
Common Objections and How to Handle Them
Enterprise buyers and internal stakeholders may raise concerns about TDX adoption.
“Is there a performance overhead?”
Reality: TDX adds approximately 1-5% performance overhead for most workloads. Memory-intensive workloads may see slightly higher overhead. For most applications, this is imperceptible.
Response: “Yes, there’s a small performance overhead, typically 1-5%. For enterprise customers, this trade-off makes sense because the security benefits far outweigh minor performance impacts. We’ve benchmarked our workloads and the overhead is negligible for our use cases.”
Share performance benchmarks showing real-world impacts on your specific workloads.
“This seems complex to implement”
Reality: Initial implementation requires engineering effort, but it’s not a complete architecture overhaul. Most companies implement TDX in 2-4 weeks.
Response: “Implementation takes 2-4 weeks for experienced teams. We work with OpenMetal’s support team who have done this many times. It’s not a rewrite of our application – we’re adding a security layer. The business value from landing enterprise deals justifies the implementation effort.”
“Can’t we just use public cloud confidential computing?”
Reality: Public clouds offer confidential computing but with limitations: shared hardware, hypervisor dependencies, variable costs, less control.
Response: “Public cloud confidential computing exists but runs on shared hardware with additional virtualization layers. Bare metal TDX provides stronger isolation because we control the entire stack. We also get better cost predictability and performance. For our enterprise customers, the additional control matters.”
“Our current customers don’t ask for this”
Reality: Small and mid-market customers often don’t ask about advanced security features. Enterprise customers have different requirements.
Response: “You’re right that current customers don’t ask. That’s because we’re targeting a different customer segment. Enterprise buyers have security teams that require these capabilities. This investment enables us to pursue enterprise deals worth 10x our current average contract size.”
“What if Intel discovers a vulnerability in TDX?”
Reality: No technology is perfect. TDX provides defense-in-depth, not absolute security.
Response: “Intel maintains a responsible disclosure program for security issues. TDX provides additional protection layers beyond what we have without it. If a vulnerability emerges, we can patch quickly. Even with potential future vulnerabilities, TDX is significantly stronger than standard virtualization security.”
Wrapping Up: Using TDX to Win Enterprise Deals
Mid-market SaaS companies face a clear choice when pursuing enterprise growth. You can compete without confidential computing and hope your product features alone close deals, or you can remove a major competitive barrier by implementing Intel TDX.
The business case is straightforward: infrastructure investment of roughly $50-80K annually enables you to pursue enterprise contracts worth $300-600K each. Most companies close at least one additional enterprise deal with TDX as a differentiator, creating immediate positive ROI.
Beyond direct revenue impact, TDX positions your company as technically advanced, security-forward, and enterprise-ready. This creates competitive advantages that compound over time. Enterprise buyers remember which vendors had the security capabilities they needed and which didn’t.
The companies winning enterprise deals in 2026 are those that recognized earlier how security requirements were changing and built infrastructure to meet those requirements. Intel TDX on bare metal infrastructure provides the capabilities enterprise buyers actually require, not just security theater that sounds good in marketing materials.
Whether you’re facing RFPs you can’t answer, losing competitive deals to more secure competitors, or simply trying to break into enterprise accounts, confidential computing opens doors that remain closed without it.
Ready to deploy Intel TDX? Explore OpenMetal’s confidential computing infrastructure or contact the team to discuss implementing TDX for your enterprise sales needs.
Pricing current as of February 2026 and subject to change. View current pricing.
Schedule a Consultation
Get a deeper assessment and discuss your unique requirements.
Read More on the OpenMetal Blog



































