OpenStack is unique in that it has use cases that range from how a smaller tech business might use a private cloud, to a telecom that needs Network Function Virtualization for their 5G customers, to massive scale distributed public cloud services.
The breadth of use cases brings functionality to all of the users though. In this post (a work in progress so don’t pick too much on the details yet) I will walk through how OpenStack supports running geographically separated OpenStacks from one central command OpenStack.
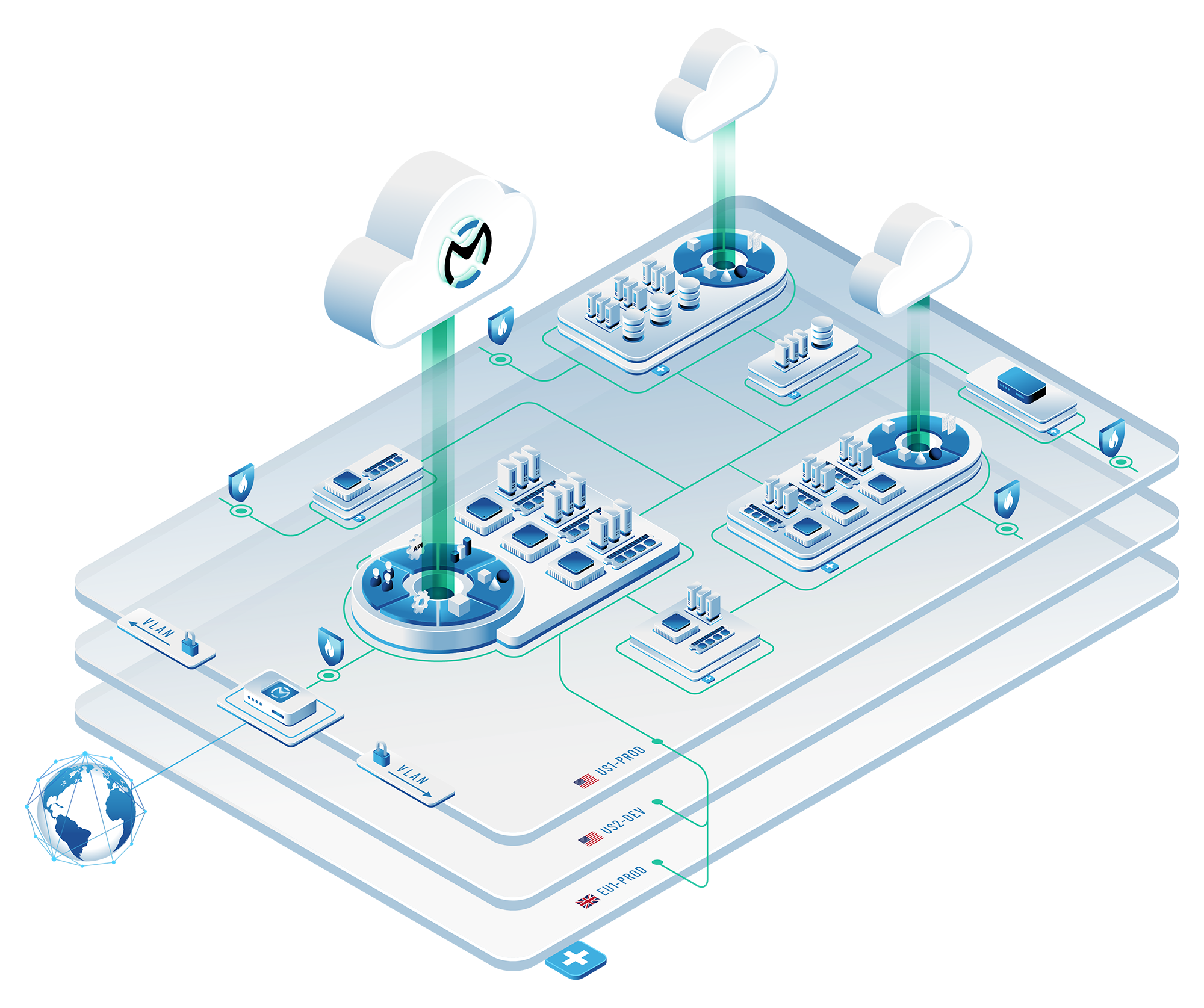
But first, the OpenMetal “super graphic” to help us understand this.
Trying to get onto your own cloud?
- Check out our On-Demand OpenStack
- Transparent Cloud Pricing
- Great Team!
Representation of a Federated OpenStack
This graphic represents one OpenStack, labeled US1-Prod that is controlling user access to EU1-Prod and US2-Dev via Keystone Federation. Within each of the separate Clouds (US1-Prod, EU1-Prod, US2-Dev) there are full HA control plane nodes (Cloud Cores) that handle the services for that Cloud. For example, Private Networks for VMs and Storage in EU1-Prod are handled by the Cloud Core of EU1-Prod. US1-Prod does provide the User Authentication, APIs, GUI (Horizon), and a few other items.
US1-Prod does not handle any of the EU1-Prod networking by default as that would create latency. Virtual Private Network Site to Site VPNs can provide that if needed.
For more reading check out the OpenStack.org Guide or schedule a meeting with us to discuss.
Test Drive
For eligible organizations, individuals, and Open Source Partners, Private Cloud Cores are free of charge. Apply today to qualify.
Subscribe
Join our community! Subscribe to our newsletter to get the latest company news, product releases, partner updates, and more.
Follow Us
Follow OpenMetal and the team on LinkedIn and share our passion for OpenStack, On-Demand Private Clouds, open source, and more!