In This Article
Payment processors face a challenge: building infrastructure that passes PCI DSS 4.0.1 audits without creating operational complexity or unpredictable costs. As of March 2025, enhanced authentication, stricter encryption, and comprehensive network segmentation became mandatory. This guide explains how infrastructure architecture directly impacts compliance scope and costs, and why dedicated hardware with physical network isolation simplifies audits while reducing the systems requiring remediation.
Your payment processing infrastructure needs to pass PCI DSS audits without creating operational nightmares or unpredictable costs. As of March 31, 2025, all formerly “best practice” requirements in PCI DSS 4.0.1 became mandatory. Payment processors and fintech companies now face enhanced authentication requirements, stricter encryption standards, and comprehensive network segmentation testing, all while maintaining the performance and reliability customers expect.
The infrastructure decisions you make today determine whether your next PCI assessment reveals hundreds of in-scope systems requiring remediation or a tightly controlled cardholder data environment (CDE) that passes audits efficiently. This guide explains how infrastructure architecture directly impacts PCI compliance and how dedicated hardware provides the control auditors look for.
Why Infrastructure Architecture Determines PCI Compliance Costs
PCI DSS doesn’t mandate specific infrastructure choices, but your architecture decisions ripple through every requirement. The Payment Card Industry Security Standards Council defines scope based on system components that store, process, or transmit cardholder data, plus any systems that could impact the security of those components. According to the PCI DSS v4.0.1 standard, this includes “system components, people, and processes that store, process, or transmit cardholder data and/or sensitive authentication data” as well as “system components that could impact the security of the cardholder data environment”. Poor architectural boundaries turn routine compliance into expensive remediation projects.
Public cloud environments introduce complexity that makes demonstrating isolation difficult during assessments. When virtualization layers share physical hardware across multiple tenants, auditors scrutinize hypervisor security, shared memory protections, and side-channel attack mitigations. These concerns disappear with dedicated infrastructure where physical isolation provides demonstrable security boundaries.
Network segmentation reduces PCI scope by isolating the CDE from non-payment systems. According to PCI DSS guidance on modern network architectures, effective segmentation can dramatically reduce the time, effort, and cost of assessments. However, segmentation only works when you control the underlying network topology. Shared infrastructure limits your ability to implement physical separation or customize firewall configurations that prove network boundaries to qualified security assessors.
Organizations using dedicated infrastructure report faster audit preparation because they provide assessors with clear answers about physical and logical boundaries. When you own the network switches, control VLAN configurations, and manage firewall rules without vendor restrictions, demonstrating compliance becomes straightforward documentation rather than elaborate explanation.
The 12 Requirements and Your Infrastructure Choices
PCI DSS 4.0.1 organizes security controls into 12 requirements. Your infrastructure architecture either supports or complicates compliance with each one.
Requirements 1-2: Network Security and Configuration Standards
Network firewalls must restrict traffic between the CDE and untrusted networks. Requirement 1 demands documented data flow diagrams showing exactly how payment data moves through your environment. On shared infrastructure, mapping these flows means accounting for virtualization layers, shared network services, and multi-tenant routing, complexities that audit teams scrutinize heavily.
Dedicated infrastructure simplifies network security documentation. Physical network devices with explicit VLAN configurations and dedicated routing tables provide auditors with clear evidence of network segmentation. You control firewall rules at both the network perimeter and between internal segments without navigating vendor-managed network services or shared security groups.
Configuration management requirements demand that default passwords get changed, unnecessary services get disabled, and security configurations get documented. These seemingly simple requirements become complex in environments where you share management platforms with other tenants or where vendor-managed services control portions of your infrastructure.
Requirement 3: Protect Stored Cardholder Data
Data encryption requirements specify strong cryptography for data at rest. PCI DSS 4.0.1 clarifies that when using cryptographic hashes to protect primary account numbers (PAN), organizations must implement keyed cryptographic hashes with proper key management processes.
Infrastructure impacts encryption compliance in several ways. Dedicated hardware enables hardware security modules (HSMs) for cryptographic key management, a control that significantly strengthens your security posture during assessments. Bare metal servers with direct-attached NVMe storage simplify encryption-at-rest implementations because you control the entire storage stack without virtualization layers that could expose unencrypted data in hypervisor memory.
Storage architecture affects retention and disposal requirements under Requirement 3.2. When cardholder data exists in multiple locations (database servers, backup systems, log files, development environments), tracking and purging becomes complex. Consolidating storage on infrastructure you control makes data lifecycle management auditable.
Requirements 4-6: Encryption, Patching, and Secure Development
In-transit encryption requirements mandate strong cryptography for cardholder data transmission across public networks. This seems straightforward until you consider how data flows through load balancers, API gateways, and internal service meshes. Shared infrastructure often terminates SSL/TLS at vendor-managed load balancers where you can’t inspect certificate management or cipher configurations.
Vulnerability management under Requirement 6 demands authenticated scanning, a new mandatory requirement as of March 2025. Authenticated scans require credentials to access systems for deeper vulnerability assessment. Providing scan credentials in multi-tenant environments creates security concerns. Dedicated infrastructure allows vulnerability scanning without exposing credentials to shared management platforms.
Patch management becomes simpler when you control the entire software stack. Bare metal and private cloud deployments let you schedule maintenance windows, test patches thoroughly, and deploy updates on your timeline rather than coordinating with cloud provider maintenance schedules that might not align with PCI requirements.
Requirements 7-8: Access Control and Authentication
Access control requirements specify role-based access control (RBAC) and the principle of least privilege. Requirement 7 demands that access to cardholder data gets restricted to those whose jobs require it, a control that requires detailed access logs and permission audits.
Multi-factor authentication (MFA) requirements expanded significantly in PCI DSS 4.0.1. As of the March 2025 deadline, MFA is mandatory for all access to the CDE, not just remote access or administrative users. This includes:
- All administrative access to system components
- All non-console access to the CDE
- All remote network access originating from outside the entity’s network
- Cloud-based system components, both administrative and user access
Infrastructure architecture directly impacts MFA implementation complexity. Dedicated infrastructure allows consistent MFA enforcement across all access methods through centralized identity management. Shared environments often require navigating multiple authentication systems, cloud provider consoles, management APIs, service accounts, each with different MFA capabilities.
Password requirements specify minimum 12-character passwords combining alphanumeric characters. Service provider requirements add password rotation unless dynamic analysis detects potentially compromised credentials. These authentication controls require infrastructure that logs all authentication attempts, supports centralized identity management, and integrates with security information and event management (SIEM) systems for behavioral monitoring.
Requirement 9-10: Physical Security and Logging
Physical security requirements specify restricted access to facilities housing cardholder data. Data center certifications become audit evidence. OpenMetal operates in Tier III data centers with SOC 1, SOC 2, SOC 3, PCI-DSS, NIST 800-53/FISMA, HIPAA, ISO 27001, ISO 22301, ISO 50001, and LEED Gold certifications. These certifications satisfy physical security requirements without organizations needing to maintain their own compliant facilities.
Logging requirements under Requirement 10 specify comprehensive audit trails for all access to cardholder data and security-relevant events. Logs must be centralized, tamper-resistant, and retained for at least 12 months with three months immediately available for analysis. Infrastructure choices determine whether log aggregation happens within your control or whether logs flow through vendor-managed systems where retention policies might conflict with PCI requirements.
Dedicated infrastructure enables comprehensive logging without bandwidth concerns or log export fees. You control log storage duration, implement write-once storage for tamper resistance, and integrate logging directly with SIEM platforms that perform the real-time monitoring PCI DSS 4.0.1 emphasizes.
Requirements 11-12: Testing, Monitoring, and Security Policies
Security testing requirements expanded in PCI DSS 4.0.1. Organizations must conduct internal and external vulnerability scans quarterly and after significant changes. Network segmentation controls require testing every six months and after any changes to segmentation architecture.
Penetration testing must occur annually and after significant infrastructure changes. Dedicated infrastructure simplifies penetration testing because security assessors can thoroughly test without concerns about impacting other tenants or violating cloud provider acceptable use policies. You control the testing schedule and scope without coordinating with vendors.
Requirement 12 demands comprehensive security policies, security awareness training, and incident response plans. These policies reference specific infrastructure controls, making infrastructure architecture documentation essential. Clear documentation of network topology, system ownership, and security responsibilities becomes simpler when you control the entire stack rather than stitching together responsibilities across multiple service providers.
Network Segmentation: The Scope Reduction Strategy
Network segmentation isn’t mandatory under PCI DSS, but it remains the most effective way to reduce compliance scope and contain security incidents. The PCI Security Standards Council’s guidance on modern network architectures emphasizes that effective segmentation dramatically reduces assessment scope by isolating the CDE from non-payment systems.
How Segmentation Reduces Scope
Every system in your network starts as potentially in-scope for PCI DSS. Through network segmentation, you prove to auditors that certain systems cannot impact CDE security even if compromised. This proof requires demonstrating:
Physical or logical separation: Dedicated infrastructure provides both. Physical separation through distinct network interfaces and switches creates boundaries auditors can verify physically. Logical separation through VLANs backed by dedicated hardware provides clear network-layer isolation.
Firewall controls between segments: Requirement 1 specifies firewall configurations that restrict traffic between segments. You must document what traffic flows between zones and why. Dedicated network hardware allows granular firewall rules that precisely match documented policies.
Continuous monitoring and testing: Requirement 11.4.5 mandates segmentation testing every six months and after changes. Testing verifies that firewall rules, router ACLs, and network architecture actually prevent unauthorized traffic between segments. Dedicated infrastructure simplifies testing because you control the testing environment completely.
Limited trust relationships: Segmentation fails if systems outside the CDE have service accounts, API access, or administrative credentials that could pivot into payment systems. Dedicated infrastructure allows strict control over authentication mechanisms and service-to-service communication.
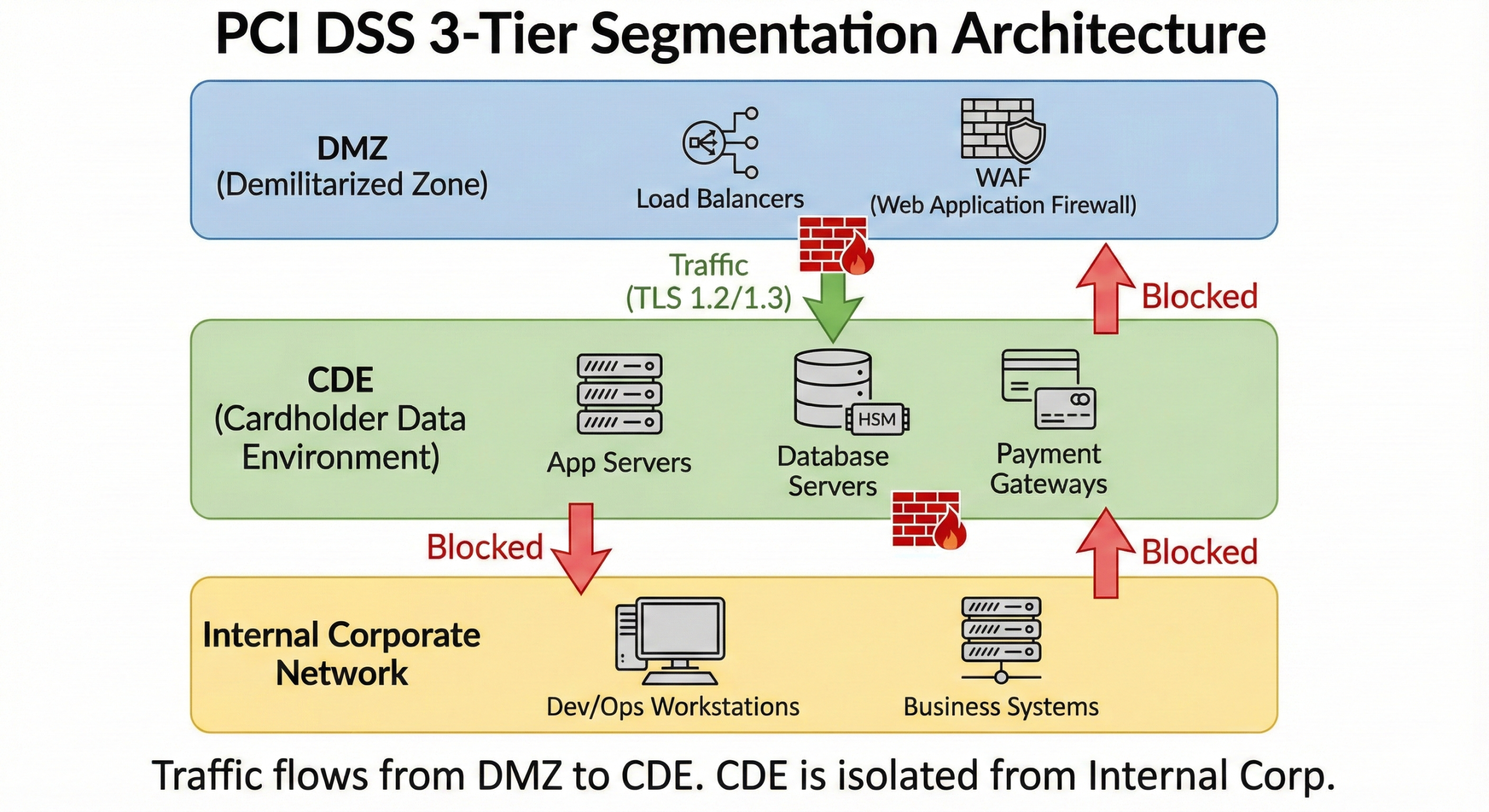
Segmentation Architecture Patterns
Payment processors typically implement three-tier segmentation:
DMZ (demilitarized zone): Internet-facing systems that receive payment data but don’t store it. Web servers, API gateways, and load balancers sit here. This segment has strict ingress/egress rules and extensive logging.
CDE core: Payment databases, payment gateways, and authorization systems. This segment has the strictest controls with no direct internet access. Traffic enters only through the DMZ with application-layer filtering.
Internal corporate network: Out-of-scope systems for operations, development, and business functions. Segmentation prevents lateral movement from potentially compromised workstations into payment systems.
Dedicated infrastructure enables this architecture through:
- Physical network interfaces dedicated to each tier
- Separate VLANs with dedicated switches or switch configurations
- Firewall appliances or host-based firewalls controlling inter-segment traffic
- Monitoring infrastructure that observes all inter-segment communication
Public cloud environments require elaborate network configurations, security groups, and service mesh implementations to achieve similar segmentation, and auditors scrutinize these logical controls more heavily because they lack physical verification points.
 protect
protect
Segmentation Testing and Documentation
PCI DSS Requirement 11.4.5 specifies that segmentation controls must be tested at least every six months and after any changes to segmentation architecture. Testing proves that firewall rules, router configurations, and network architecture actually prevent unauthorized access between segments.
Testing methodology includes:
Port scanning from out-of-scope systems: Verify that CDE systems aren’t reachable from corporate networks. Dedicated infrastructure allows unrestricted port scanning without violating terms of service.
Penetration testing of segmentation boundaries: Security assessors attempt to move laterally between segments. Physical network boundaries provide clear testing targets.
Configuration reviews: Document and verify firewall rules, ACLs, and routing tables. Dedicated hardware means these configurations exist in files you control rather than vendor-managed abstractions.
Change management integration: Any network changes trigger retesting. When you control network hardware, change tracking becomes straightforward.
Comprehensive segmentation documentation satisfies auditor requirements by clearly showing:
- Network topology diagrams with segment boundaries
- Data flow diagrams showing exactly how payment data moves between segments
- Firewall rule documentation explaining why each rule exists
- Testing results proving controls work as documented
OpenMetal’s network architecture supports PCI segmentation requirements through dedicated VLANs providing physical broadcast domain isolation. Dual 10 Gbps NICs provide 20 Gbps aggregate bandwidth for private networking, enabling high-throughput internal payment processing without network contention. Full root access allows customizing network configurations to match specific segmentation requirements.
Infrastructure Control Requirements That Favor Dedicated Hardware
Several PCI DSS requirements become significantly simpler with infrastructure you control completely.
Multi-Factor Authentication Implementation
MFA became mandatory for all CDE access as of March 2025. Implementation challenges include:
- Consistent MFA across all access methods (console, API, web interfaces)
- MFA systems resistant to replay attacks and man-in-the-middle attacks
- Centralized authentication logging for audit trails
Dedicated infrastructure allows implementing identity providers (IdPs) within your network perimeter. You control authentication systems completely, enforce MFA at the network edge, and maintain comprehensive authentication logs without relying on multiple vendor authentication systems.
Encryption Key Management
Requirement 3 emphasizes proper key management for cryptographic operations. Hardware security modules (HSMs) provide tamper-resistant key storage and cryptographic operations. Bare metal servers support PCIe HSM cards for dedicated cryptographic acceleration within your infrastructure, eliminating concerns about key exposure in multi-tenant environments. Advanced security features like Intel TDX provide hardware-level encryption for data in use, adding another layer of protection for payment processing workloads.
Patch Management and Change Control
Requirement 6 mandates patching critical vulnerabilities within one month of release. Meeting this deadline requires test environments that accurately reflect production, controlled maintenance windows, and the ability to roll back failed patches.
Dedicated infrastructure supports comprehensive patch testing because you create exact replicas of production configurations. Maintenance windows happen on your schedule without coordinating across vendor maintenance schedules. Rollback procedures use infrastructure-level snapshots or bare metal re-imaging rather than depending on cloud provider backup systems.
Security Monitoring and Log Management
Requirement 10 specifies comprehensive logging with tamper-resistant storage. Log aggregation systems must collect logs from all in-scope systems, maintain logs for required retention periods, and provide real-time analysis capabilities.
Dedicated infrastructure eliminates log export fees and bandwidth constraints that limit comprehensive logging in pay-per-use environments. You implement centralized logging infrastructure within your network, control log retention completely, and integrate logging with SIEM platforms without data egress concerns.
Incident Response and Forensics
PCI DSS Requirement 12.10 demands incident response plans and forensic investigation capabilities. Effective incident response requires:
- Network packet captures for forensic analysis
- Detailed system logs showing exactly what happened
- Ability to isolate compromised systems immediately
- Forensic disk images of affected systems
Dedicated infrastructure supports incident response through network monitoring that captures all traffic, immediate system isolation through network controls you manage, and forensic procedures that don’t require coordinating with cloud providers whose incident response processes might conflict with your investigation needs.
OpenMetal Infrastructure for PCI Compliance
OpenMetal provides bare metal servers and hosted private cloud that support PCI DSS compliance requirements through:
PCI-DSS certified data centers: Facilities maintain certifications that satisfy physical security requirements under Requirement 9. Data center audits become reference documents rather than organizational responsibilities.
Dedicated hardware with full root access: Complete control over operating systems, security configurations, and network topology. Install specific security tools, implement custom network architectures, and enforce configurations that match your security policies exactly.
Network isolation through dedicated VLANs: Physical network segmentation that provides clear boundaries for auditor verification. No shared network infrastructure means segment isolation you can demonstrate physically.
Predictable fixed costs: PCI compliance assessment scope directly impacts costs. Fixed infrastructure pricing allows accurate budgeting for compliance-related infrastructure rather than variable costs that fluctuate with usage during assessment periods.
Flexible deployment options: Choose between bare metal for applications requiring direct hardware access (like HSMs) or hosted private cloud built on OpenStack for environments needing virtualization within your dedicated hardware. Both provide the control compliance requires.
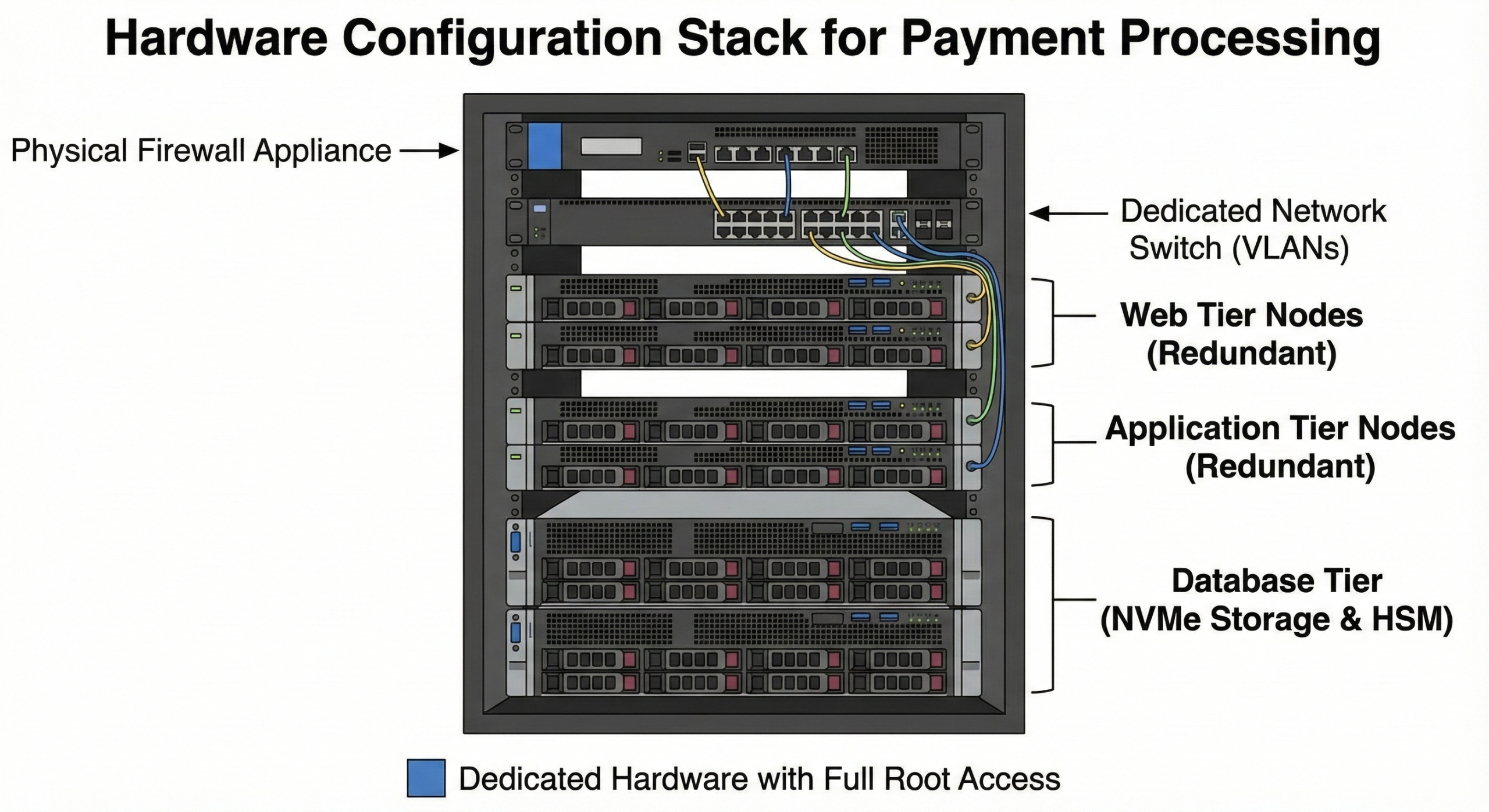
Hardware Configurations for Payment Processing
Payment processors typically choose infrastructure based on transaction volume and redundancy requirements:
Small to medium payment processors (up to 100,000 transactions/day):
- Medium v4 bare metal servers (32 cores, 256GB RAM, 1.92TB NVMe)
- Three-node configuration: web tier, application tier, database tier
- Dedicated VLAN for CDE isolation
- Hardware firewall or dedicated firewall server
Large payment processors (100,000+ transactions/day):
- Large or XL v4 servers for database tier (high-memory configurations)
- Multiple web/application servers for redundancy
- Hosted Private Cloud for easier scaling and management
- Multi-region deployment for disaster recovery
High-availability requirements:
- Minimum 5-node clusters spanning two availability zones
- Load balancers with failover capability
- Real-time database replication
- Comprehensive monitoring infrastructure
Cost Predictability for Compliance
PCI DSS compliance creates cost uncertainty in usage-based infrastructure. Assessment preparation drives increased logging, security scanning, penetration testing, and backup operations, all activities that generate variable costs in public cloud environments.
Fixed monthly costs based on dedicated hardware eliminate these variables. Budget accurately for:
- Compliance assessment periods requiring intensive logging
- Quarterly vulnerability scanning
- Annual penetration testing
- Backup and disaster recovery testing
- Development and testing environments that mirror production
OpenMetal’s 95th percentile bandwidth pricing accommodates occasional compliance-related traffic spikes without penalty. Data transfer for log replication, backup operations, or security tool communications doesn’t create surprise bills.
When Dedicated Infrastructure Makes Sense for PCI Compliance
Not every payment processor requires dedicated infrastructure, but several indicators suggest it’s the right choice:
Transaction volume exceeds 100,000 monthly: PCI DSS Level 2 merchants (1-6 million transactions annually) face comprehensive assessment requirements. Infrastructure that simplifies assessments provides immediate ROI through reduced audit costs and faster remediation.
Multiple service provider relationships: Organizations providing payment services to other companies face service provider requirements including semi-annual scope documentation and Executive management involvement. Clear infrastructure boundaries simplify these requirements.
Custom payment flows: Standard payment gateways handle common scenarios well, but specialized payment processing (subscription billing, complex authorization logic, installment payments) benefits from infrastructure you control completely. Custom application development requires infrastructure where you implement security controls without vendor restrictions.
Regulatory requirements beyond PCI: Organizations in healthcare (HIPAA), finance (SOC 2), or government sectors (NIST 800-53) benefit from infrastructure that supports multiple compliance frameworks. Dedicated hardware satisfies physical isolation requirements across different standards.
High-value transactions: Payment processors handling large transaction values face greater scrutiny during PCI assessments. Demonstrating comprehensive controls becomes easier with infrastructure providing physical verification points rather than relying entirely on logical controls.
Strong in-house technical teams: Organizations with experienced system administrators, security engineers, and DevOps teams benefit most from infrastructure control. Dedicated hardware maximizes their expertise by removing vendor-imposed limitations.
Implementation Roadmap for PCI-Compliant Infrastructure
Building compliant payment processing infrastructure follows a phased approach:
Phase 1: Assessment and Planning (Weeks 1-4)
Document current state: Map existing payment data flows, identify all systems touching cardholder data, inventory current controls.
Define future state architecture: Design network segmentation strategy, select hardware configurations, plan migration approach.
Gap analysis: Compare current controls against PCI DSS 4.0.1 requirements, prioritize remediations, estimate implementation timeline.
Phase 2: Infrastructure Deployment (Weeks 5-8)
Deploy core infrastructure: Provision bare metal servers or private cloud clusters, configure network segmentation with dedicated VLANs, implement firewall rules between segments.
Build security infrastructure: Deploy centralized logging infrastructure, configure vulnerability scanning systems, establish backup and monitoring platforms.
Set up access controls: Implement identity provider for MFA, configure role-based access control, establish privileged access management.
Phase 3: Application Migration (Weeks 9-14)
Migrate payment systems: Move payment applications to new infrastructure, configure encryption for data at rest and in transit, test payment processing functionality thoroughly.
Establish testing environment: Create development and staging environments within segmented networks, implement change management processes, document application configurations.
Security hardening: Disable unnecessary services, change default credentials, apply security patches, configure host-based firewalls.
Phase 4: Compliance Validation (Weeks 15-18)
Internal assessment: Conduct internal PCI self-assessment questionnaire (SAQ) or engage internal auditors, document all security controls, address identified gaps.
Penetration testing: Engage qualified security assessors for external penetration testing, test network segmentation controls, document test results.
Pre-audit preparation: Compile compliance documentation, organize evidence of security controls, schedule qualified security assessor (QSA) engagement.
Phase 5: Ongoing Operations
Quarterly vulnerability scanning: Schedule and conduct internal and external scans, remediate critical vulnerabilities within one month, document scan results.
Semi-annual segmentation testing: Verify network segmentation controls remain effective, update documentation reflecting any changes, engage assessors for formal testing.
Annual compliance assessment: Complete PCI DSS report on compliance (ROC) with QSA, address audit findings, update security policies and procedures.
Continuous monitoring: Review security logs daily, respond to security alerts promptly, maintain inventory of all in-scope systems.
Getting Started With PCI-Compliant Infrastructure
Payment processing demands infrastructure that passes audits without creating operational complexity or cost uncertainty. PCI DSS 4.0.1 requirements favor architectures providing clear physical and logical boundaries, comprehensive logging, and security controls you demonstrate easily during assessments.
Dedicated infrastructure, whether bare metal servers or private cloud built on dedicated hardware, provides the control compliance requires. Physical network segmentation, unrestricted security tool deployment, and complete access to logs and configurations eliminate the abstractions that complicate assessments in shared environments.
OpenMetal’s bare metal and hosted private cloud solutions give payment processors infrastructure designed for compliance-intensive workloads. PCI-DSS certified data centers, dedicated VLANs for network isolation, and fixed monthly costs provide the foundation for compliant payment processing infrastructure that scales with your business.
Ready to build infrastructure that simplifies PCI compliance? Contact OpenMetal’s infrastructure team to discuss your payment processing requirements and design architecture that passes audits efficiently while supporting your business goals.
Schedule a Consultation
Get a deeper assessment and discuss your unique requirements.
Read More on the OpenMetal Blog